
Kaspersky Introduces iShutdown for Detecting Pegasus and Enhancing iPhone Security
Kaspersky's Innovative Tool to Counter iOS Spyware Threats
NEWS Security January 22, 2024 Reading time: 2 Minute(s)
In the wake of Kaspersky cybersecurity researchers uncovering crucial insights into Operation Triangulation, a groundbreaking tool has emerged to bolster iPhone security. Kaspersky’s Global Research and Analysis Team (GReAT) has unveiled the iShutdown tool, designed to detect notorious iOS spyware, including the well-known Pegasus, QuaDream’s Reign, and Intellexa’s Predator.
The iShutdown tool, released to the public seven months after Kaspersky Labs reported the hacking of its employees' iPhones in Operation Triangulation, offers users a lightweight yet effective method to identify signs of spyware on Apple iOS devices. Unlike the iShutdown iOS application for Mac devices, this tool focuses specifically on detecting and countering spyware threats.
During testing on Pegasus-compromised iPhones, the method proved its efficacy. Notably, it differentiates itself from the iShutdown iOS application, which is intended for controlling Mac device functions such as shutdown, sleep, restart, and log out.
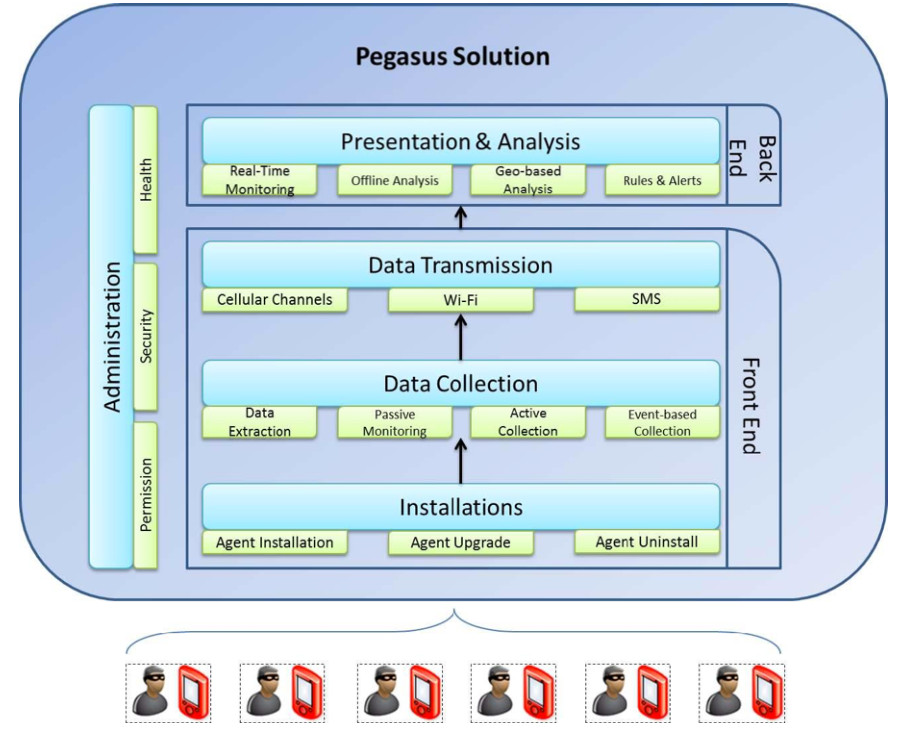
HIGHLEVEL ARCHITECTURE DIAGRAM OF PEGASUS SPYWARE
The tool leverages a unique approach by analyzing a text-based system log file called "Shutdown.log" found in the sysdiagnose archive of iOS devices. This forensic artifact records every reboot event with environmental characteristics, providing valuable information dating back several years. Traces of Pegasus-related processes were discovered in this log file, specifically in reboot delay notices, enabling the tool to accurately flag potential infections.
Further analysis revealed a common filesystem path used by all three spyware families, serving as an indicator of compromise. Kaspersky GReAT’s lead security researcher, Maher Yamout, confirmed the log's consistency with other Pegasus infections, establishing it as a reliable forensic artifact for infection analysis.
To facilitate user-friendly detection, Kaspersky has developed a Python3 utility on GitHub compatible with macOS, Windows, and Linux. The tool simplifies the extraction, analysis, and parsing of Shutdown.log artifacts, providing users with an efficient means of enhancing their digital security.
Yamout emphasized the simplicity of Shutdown.log file recovery compared to more time-consuming acquisition methods, such as forensic device imaging or a full iOS backup. However, Kaspersky advises users to adopt a holistic approach to data and device security. Recommendations include daily reboots, lockdown mode usage, disabling iMessage and FaceTime, timely iOS updates, and regular backups.
This significant announcement follows SentinelOne's report revealing the adaptability of information stealers targeting macOS to circumvent Apple's built-in antivirus technology, XProtect. The introduction of the iShutdown tool marks a crucial milestone in the ongoing battle against evolving cyber threats, providing users with a powerful ally in safeguarding their digital lives.
IMAGES: REVIEW SPACE
Kaspersky Cybersecurity iOS Spyware iShutdown Tool Pegasus Spyware QuaDream Reign Intellexa Predator iPhone Security Digital Forensics Technology News RSMax
*Our pages may contain affiliate links. If you buy something via one of our affiliate links, Review Space may earn a commission. Thanks for your support!
CATEGORIES

























COMMENTS