
LummaC2 Malware v.4.0
Employing Trigonometry to Elude Detection and Steal Sensitive Data
NEWS Security November 21, 2023 Reading time: 2 Minute(s)
In a recent discovery by Outpost24's threat intelligence team, KrakenLabs, the insidious LummaC2 v4.0 malware has emerged, utilizing advanced trigonometry to slip through security measures while pilfering sensitive data.
The malevolent LummaC2 v4.0 has evolved significantly since its debut in December 2022. Written in C language, it now employs Control Flow Flattening obfuscation to confound analysts attempting to decipher its code. Strings encryption using XOR, instead of cluttering with extraneous strings, adds an additional layer of complexity for those seeking to unravel the malware's functionality. Most notably, LummaC2 v4.0 incorporates a cutting-edge anti-sandbox technique that delays execution until it detects authentic human mouse activity.
Outpost24's researchers delved into this new evasion tactic, shedding light on how LummaC2 v4.0 meticulously scrutinizes cursor movements through trigonometric calculations. By discerning distinct patterns of human behavior, the malware adeptly distinguishes genuine users from automated analysis tools. The infostealer's dynamism is further accentuated by its support for dynamic configuration files from its Command and Control (C2) server, ensuring adaptability in varied scenarios. The incorporation of a crypter in all builds adds an extra layer of defense, signifying a concerted effort by malware developers to fortify LummaC2 v4.0 against detection and analysis.
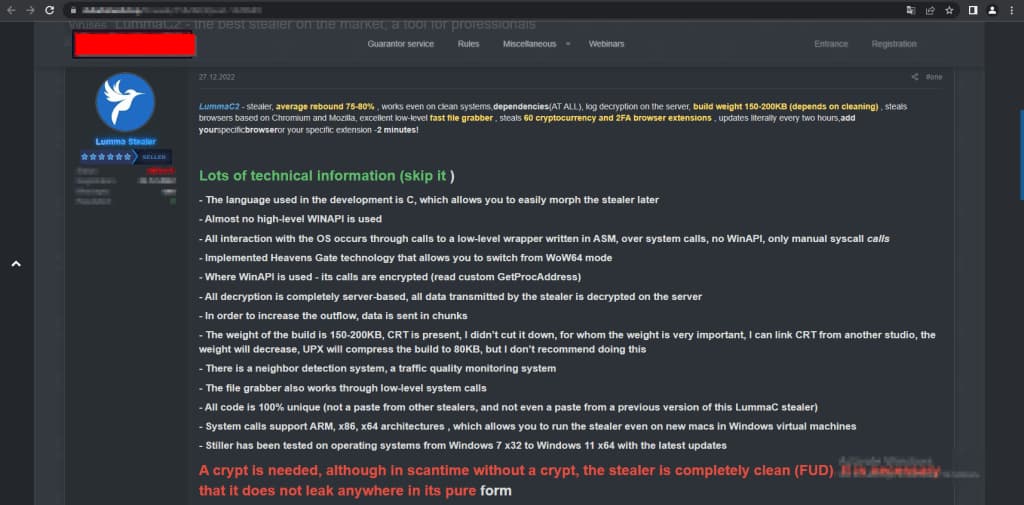
A POST BY THE AUTHOR OF THE LUMMAC2 MALWARE [Image by Outpost24]
Notably, the LummaC2 v4.0 distributor discourages the dissemination of unaltered samples, underscoring a strategic move to maintain control and stave off widespread detection.
This novel anti-sandbox technique poses a formidable challenge to cybersecurity, specifically targeting the limitations of automated mouse emulation in sandbox environments. Recognizing the persistent threat of anti-analysis techniques, organizations are urged to fortify their defenses with robust sandboxing solutions and advanced analysis techniques. Effectively detecting and analyzing obfuscated malware like LummaC2 v4.0 is crucial to safeguarding against evolving cyber threats.
Source: HackRead | Cover Image by rawpixel.com on Freepik
Malware Cybersecurity LummaC2 Trigonometry InfoStealer SecurityThreats Technology News Computer News RSNews RSMax
*Our pages may contain affiliate links. If you buy something via one of our affiliate links, Review Space may earn a commission. Thanks for your support!
CATEGORIES

























COMMENTS