
Telegram Messenger's Windows Application Vulnerability: Executable Python Scripts Masquerading as Video Files
Understanding the Recent Security Flaw and Telegram's Response
NEWS Security April 15, 2024 Reading time: 2 Minute(s)
In recent news, a security flaw has been discovered in the Windows application of the widely-used messenger, Telegram. This flaw allowed executable Python scripts to be disguised as harmless video files, potentially exposing users to security risks.
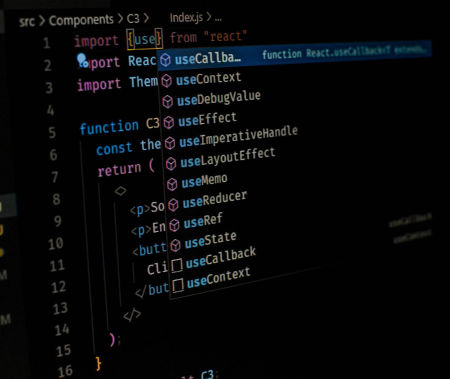 The Vulnerability
The Vulnerability
Within the source code of the Telegram Windows application, a list of file extensions triggers security warnings when clicked on. These warnings alert users to potentially harmful files, such as Windows executable files (.exe). However, due to a typographical error in the code, Python script archives with the extension ".pyzw" were not flagged, allowing them to execute without warning.
This oversight meant that if a user clicked on a disguised Python script, it would run directly on their system, provided a Python interpreter was installed.
Moreover, malicious actors could further disguise these scripts by labeling them with innocuous file types like "video/mp4", making them appear harmless to unsuspecting users.
Telegram's Response
Upon discovering the flaw, Telegram's developers swiftly addressed the issue. They acknowledged the typo in the source code and promptly rectified it on GitHub. However, as of now, an updated Windows app with the corrected code has not been released to users.

In the interim, Telegram has implemented a server-side workaround to mitigate the risk posed by the vulnerability. This workaround ensures that even in older versions of the Windows application, Python script archives will no longer execute directly. Instead, users will receive a warning message akin to the one issued for executable files, prompting them to proceed with caution.
Implications and Recommendations
While Telegram has taken proactive measures to address this security flaw, users should remain vigilant. Cybercriminals are constantly evolving their tactics, exploiting vulnerabilities wherever they arise. Therefore, it is crucial for users to exercise caution when interacting with files, especially those received through messaging platforms.
To enhance security
- Update Software: Ensure that the Telegram application is kept up-to-date to benefit from the latest security patches and fixes.
- Exercise Caution: Exercise discretion when clicking on file links, particularly those from unknown or untrusted sources.
- Install Antivirus Software: Utilize reputable antivirus software to provide an additional layer of protection against malware and malicious scripts.
- Stay Informed: Stay abreast of security advisories and news updates to remain informed about potential threats and vulnerabilities.
While the recent security flaw in Telegram's Windows application is concerning, swift action has been taken to mitigate its impact. By remaining vigilant and following best practices for cybersecurity, users can help safeguard themselves against similar vulnerabilities in the future.
IMAGES CREDITS: WIRESTOCK ON FREEPIK, FREEPIK
Telegram Messenger Online Security Windows Python Vulnerability Cybersecurity Malware Technology News RSMax
*Our pages may contain affiliate links. If you buy something via one of our affiliate links, Review Space may earn a commission. Thanks for your support!
CATEGORIES






















COMMENTS